EKS 환경에서 오브젝트(Sonarqube, ArgoCD) 배포 -1 에 이어서 작성하도록 하겠다.
gitlab-runner는 yaml로 배포하는 방식, argocd를 활용해 배포하는 방식.. 등이 있다.
2.4 GitLab Runner 배포
# helm 저장소 추가 및 업데이트
helm repo add gitlab https://charts.gitlab.io
helm repo update2.4.1 yaml로 배포하는 방식
2.4.1 .1 GitLab Personal Access Token 생성
전체 소스 코드
apiVersion: v1
kind: Namespace
metadata:
name: gitlab-runner
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: gitlab-runner
namespace: gitlab-runner
---
apiVersion: v1
kind: ConfigMap
metadata:
name: gitlab-runner-config
namespace: gitlab-runner
data:
config.toml: |
concurrent = 10
check_interval = 30
log_level = "info"
log_format = "json"
listen_address = "0.0.0.0:9252"
[session_server]
session_timeout = 1800
[[runners]]
name = "kubernetes runner"
url = "<https://gitlab.biz.com>" # GitLab URL을 변경하세요
token = "<gitlab_runner_token>" # Runner 토큰을 변경하세요
executor = "kubernetes"
[runners.kubernetes]
image = "ubuntu:20.04"
namespace = "gitlab-runner"
privileged = true
[runners.kubernetes.volumes]
[[runners.kubernetes.volumes.host_path]]
name = "gitlab-runner-logs"
mount_path = "/var/log/gitlab-runner"
host_path = "/k8s/gitlab-runner"
[runners.prometheus]
enabled = true
listen_address = "0.0.0.0:9252"
---
apiVersion: v1
kind: ConfigMap
metadata:
name: gitlab-runner-logrotate
namespace: gitlab-runner
data:
logrotate.conf: |
/var/log/gitlab-runner/*.log {
daily
rotate 7
compress
delaycompress
missingok
notifempty
copytruncate
}
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: gitlab-runner-role
namespace: gitlab-runner
rules:
- apiGroups: [""]
resources: ["pods", "pods/exec", "pods/attach", "secrets", "configmaps"]
verbs: ["get", "list", "watch", "create", "patch", "delete", "update"]
- apiGroups: [""]
resources: ["services"]
verbs: ["get", "list", "watch", "create", "update", "patch", "delete"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: gitlab-runner-rolebinding
namespace: gitlab-runner
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: gitlab-runner-role
subjects:
- kind: ServiceAccount
name: gitlab-runner
namespace: gitlab-runner
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: gitlab-runner
namespace: gitlab-runner
spec:
replicas: 1
selector:
matchLabels:
app: gitlab-runner
template:
metadata:
labels:
app: gitlab-runner
spec:
nodeSelector:
node-type: "private"
tolerations:
- key: "node-type"
operator: "Equal"
value: "private"
effect: "NoSchedule"
serviceAccountName: gitlab-runner
containers:
- name: gitlab-runner
image: gitlab/gitlab-runner:latest
imagePullPolicy: IfNotPresent
command: ["/usr/bin/dumb-init", "--", "/entrypoint", "run"]
ports:
- containerPort: 9252
name: metrics
volumeMounts:
- name: gitlab-runner-logs
mountPath: /var/log/gitlab-runner
- name: config
mountPath: /etc/gitlab-runner
readOnly: true
- name: logrotate-config
mountPath: /etc/logrotate.d/gitlab-runner
subPath: logrotate.conf
resources:
requests:
cpu: "200m"
memory: "256Mi"
limits:
cpu: "1"
memory: "1Gi"
volumes:
- name: gitlab-runner-logs
hostPath:
path: /k8s/gitlab-runner
type: DirectoryOrCreate
- name: config
configMap:
name: gitlab-runner-config
- name: logrotate-config
configMap:
name: gitlab-runner-logrotate
---
apiVersion: v1
kind: Service
metadata:
name: gitlab-runner
namespace: gitlab-runner
labels:
app: gitlab-runner
spec:
selector:
app: gitlab-runner
ports:
- name: metrics
port: 9252
targetPort: 9252
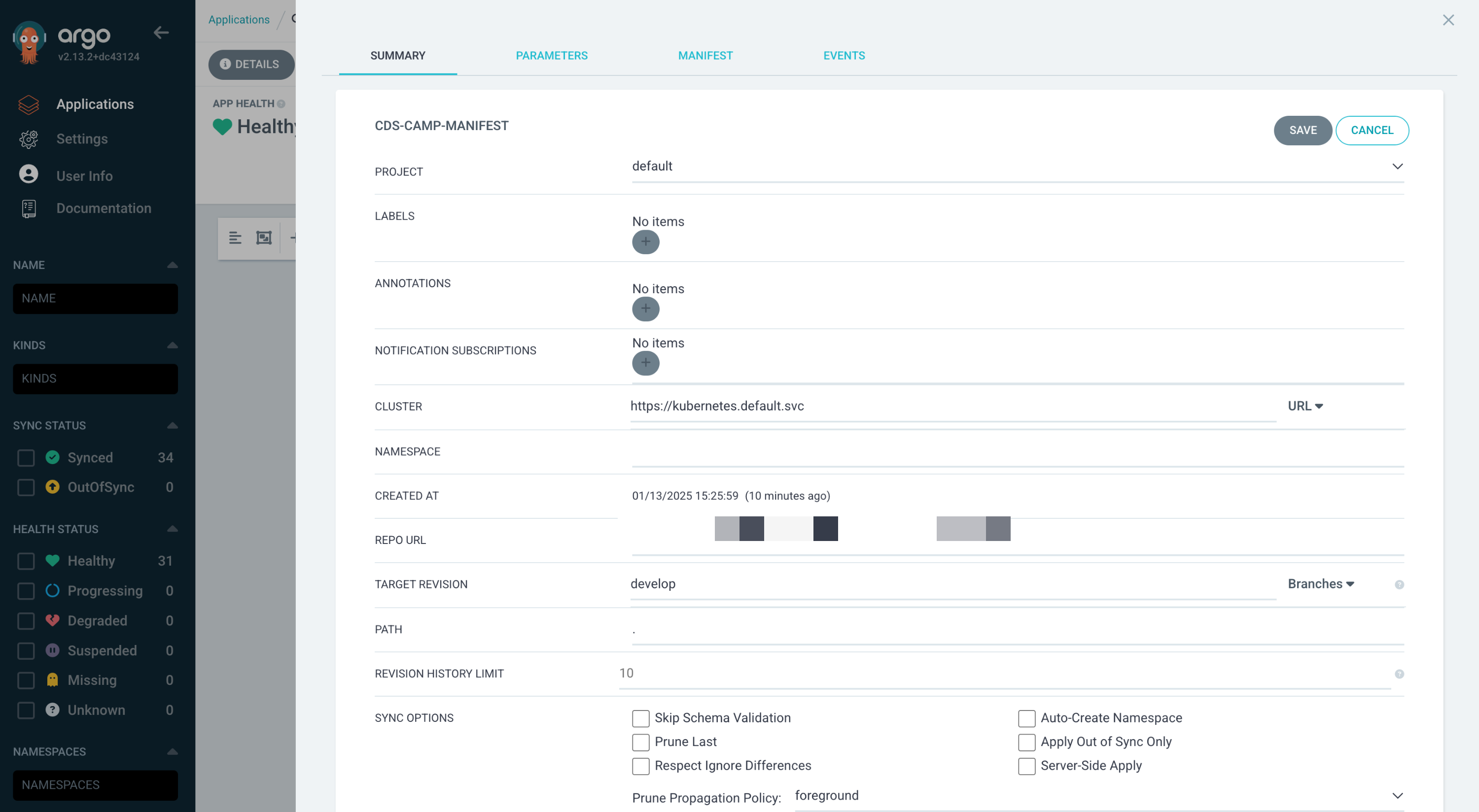
2.4.2 argocd를 활용해 배포하는 방식
Setting

+ NEW APP 클릭
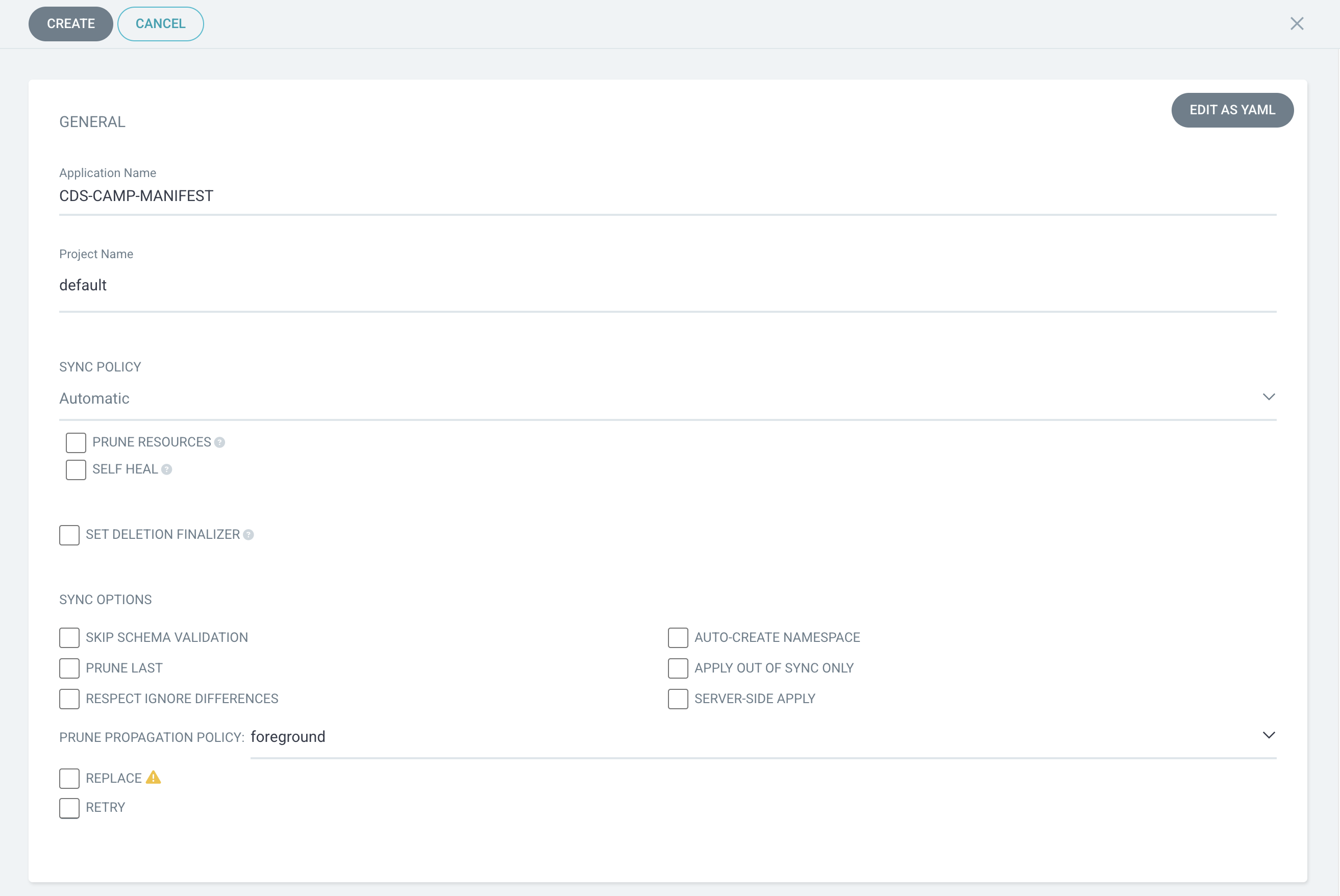
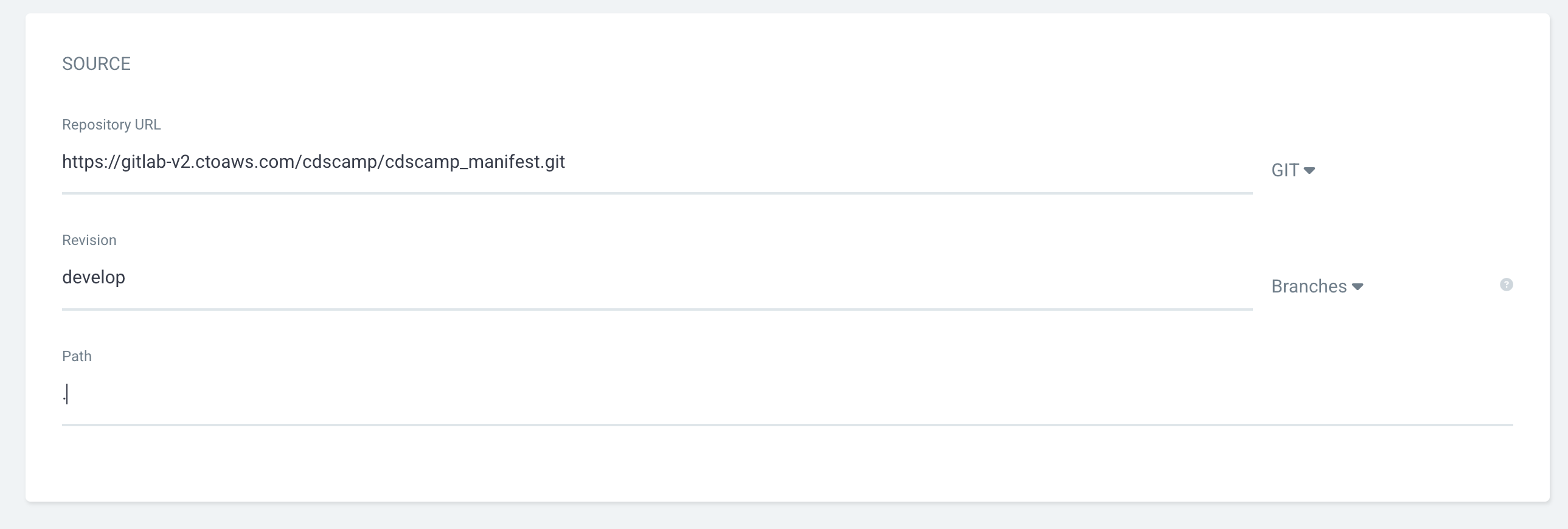
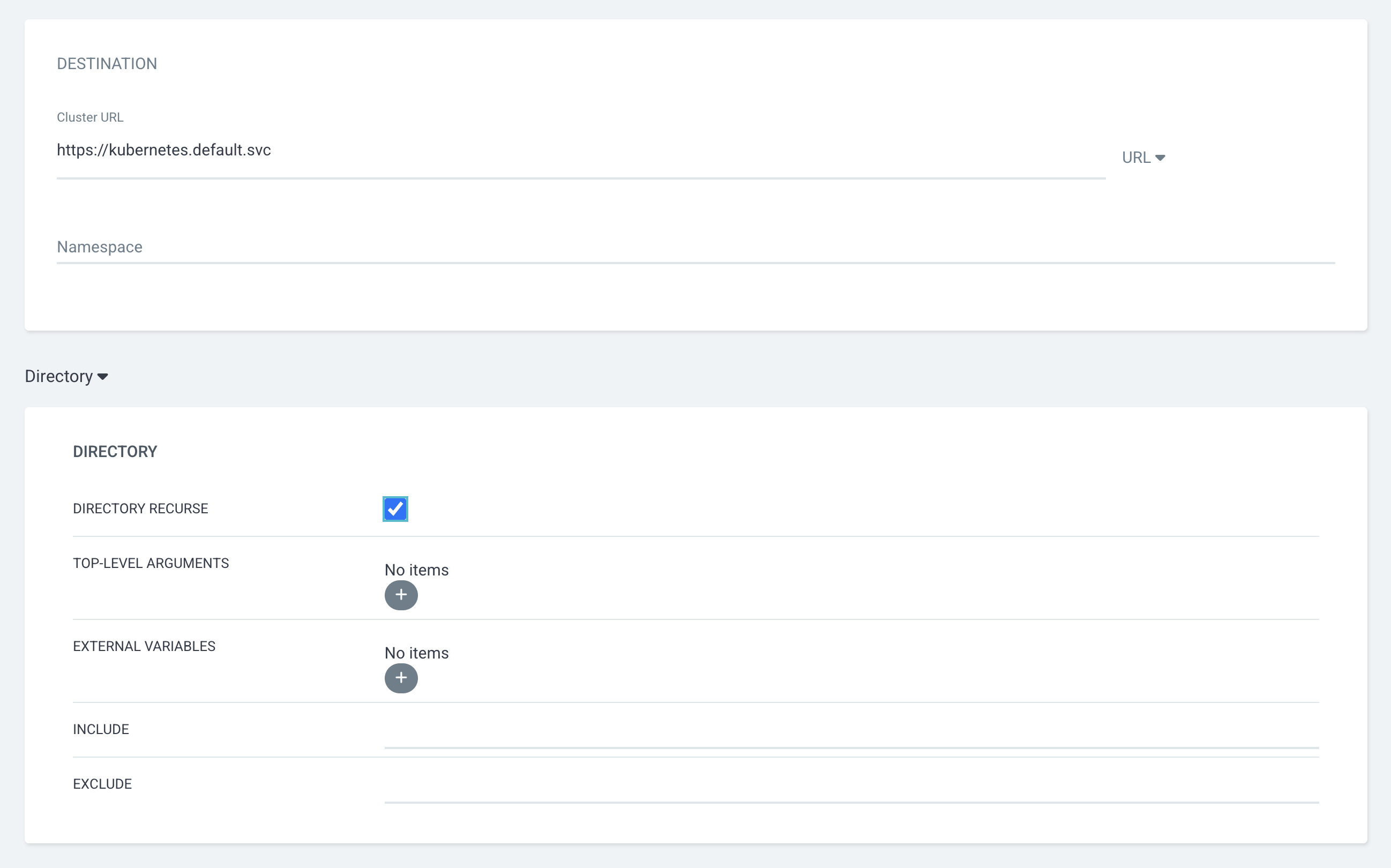
REPO URL: https://gitlab 주소.git
'IaC' 카테고리의 다른 글
| EKS 환경에서 오브젝트(Sonarqube, Argocd) 배포 -1 (0) | 2024.12.06 |
|---|---|
| [Terraform] 배포 및 플래그 (1) | 2024.06.11 |
| [Terraform] 디렉터리 구조 (0) | 2024.06.11 |
| [Terraform] 용어 (0) | 2024.04.02 |
| [Terraform] 환경 구성 (1) | 2024.04.02 |